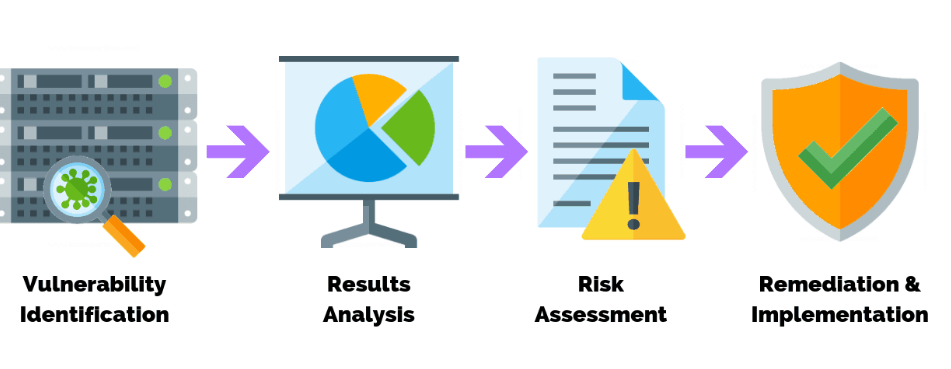
Network vulnerability assessments work to identify and rank vulnerabilities within a system. These assessments are looking for weaknesses in the system that could allow unauthorized access, flaws or susceptibility of the system, and the likelihood or capability of exploitation of the flaws. Network vulnerability assessments are often performed on information technology systems, communication systems, and other vital systems – sometimes in compliance with state or company standards and regulations. It is very similar to risk assessments there are four beginning steps to vulnerability assessment. There are also additional steps that can be taken after the preliminary steps such as the use of a vulnerability scanner. It is important for businesses and companies to conduct regular assessments in order to ensure the protection and security of their data and information.
The basic steps to vulnerability or risk assessment are cataloging resources, ranking resources, identifying vulnerabilities, and eliminating. The first step to network vulnerability assessment is to catalog your resources. By recording the different software and their assets and capabilities of a system those performing the assessment can more accurately identify problems. The second step is to rank in order of importance these assets and capabilities of the software. This allows for executives to examine overlapping capabilities and make important decisions in regards to the deletion of corrupted or vulnerable files. The next step is to assess each of the resources for their vulnerabilities and potential threats that may arise. Having this information allows business owners to evaluate the vulnerabilities in the system and begin to make any final decisions. The final step in network vulnerability assessment is to eliminate the vulnerability or fix any corruption within the systems. Unfortunately, not every vulnerability and or corruption is repairable – this is why having a list of the assets and capabilities can come in handy in determining the steps in moving forward.
https://www.gcclp.org/profile/wallabies-v-england-live-coverage-on-02-july-2022-tv/profile
https://www.cityballetsf.org/profile/wallabies-v-england-live-coverage-on-02-july-2022-tv/profile
https://www.gatewayfamilyservices.org/profile/wallabies-v-england-live-coverage-on-02-july-2022-tv/profilehttps://www.gatewayfamilyservices.orghttps://www.gatewayfamilyservices.org/profile/australia-vs-england-2022-live-on-free-broadcast-1-juli-2022-tv/profile
https://www.celebritytheatre.com/profile/australia-vs-england-2022-live-on-free-broadcast-1-juli-2022-tv/profile
https://www.cityballetsf.org/profile/australia-vs-england-2022-live-on-free-broadcast-1-juli-2022-tv/profile
https://www.gcclp.org/profile/australia-vs-england-2022-live-on-free-broadcast-1-juli-2022-tv/profile
https://www.geany.org/p/UKvQR/
https://www.geany.org/p/OPiSO/
https://paiza.io/projects/TZUGmmVXivX7jb9U0l4rhA?language=php
https://jsitor.com/-f0AIOBZd
https://dotnetfiddle.net/KhSZKv
https://ide.geeksforgeeks.org/3de6ff2d-0595-4ff0-a20e-dccb22072aaa
https://dotnetfiddle.net/Cg6UsG
https://rextester.com/TIFRT42699
http://cpp.sh/5pneg
https://jsitor.com/2DlZvkA5_
https://ide.geeksforgeeks.org/0f985708-0219-4aef-840b-0f26e7d5f406
https://jsfiddle.net/mrlive/8s3x52ud/
https://www.geany.org/p/pgXZf/
https://dotnetfiddle.net/szmRai
https://dotnetfiddle.net/3nYg7j
https://yamcode.com/mieo700um6
https://note.vg/sdfggfdf-6
https://bitbin.it/7P9Z0gLJ/
https://paste2.org/jO7sxFvU
http://paste.jp/5cd89616/
https://paste.ee/p/5w0ZE
http://pastehere.xyz/iwGkJbbHG/
https://pasteio.com/x2es4t7aJAIr
https://pasteio.com/xp3LSXhG5Azx
https://pasteio.com/xazv05rNxX3d
http://cpp.sh/2nyn
https://rentry.co/45se9
https://txt.fyi/-/22182/890461bf/
https://notes.io/qypx1
https://challonge.com/d3yp9jsu
https://ctftime.org/team/193581
https://paiza.io/projects/gK_l33sw40dJa2TSjkrcSA?language=php
https://ideone.com/1pReW8
https://tech.io/snippet/NTaa90X
https://pasteio.com/xmXLkDckKr2e
https://dotnetfiddle.net/0hEbpn
https://ide.geeksforgeeks.org/e17716ec-5579-4f67-9afa-34cba133358e
https://pastelink.net/v7q3z0a8
https://rextester.com/VTHG20548
https://paste.artemix.org/-/8YGfaG
https://pst.klgrth.io/paste/td6pm
https://wow.curseforge.com/paste/6e67edb8
https://www.wowace.com/paste/d2ae4f4d
https://paste.toolforge.org/view/f226e6f7
http://cpp.sh/5xuwot
http://cpp.sh/9tgju
https://mrlive.cookpad-blog.jp/articles/732336
https://techplanet.today/post/livestream-australia-vs-england-live-free-broadcast-on-01-july-2022
https://www.bankier.pl/forum/temat_game-live-on,55402453.html
https://www.bankier.pl/forum/temat_dshmghfg,55402461.html
https://paiza.io/projects/KxAnmMxAkrXtiWHnaX00XA?language=php
https://www.coveredgoods.com/blogs/news/7-steps-to-planning-an-easter-egg-hunt-for-kids?comment=125452353721#comments
https://eyeart.com.au/blogs/eye-art-studio-the-blog/dannis-eyebrow-tattoo-correction-how-we-helped-repair-her-eyebrow-tattoo?comment=129349517468#comments
http://cpp.sh/8om2u
http://cpp.sh/4ykmr
Another step in network vulnerability assessment is the use of a vulnerability scanner. A vulnerability scanner is a computer program that is designed to sweep and assess computer systems, networks, and or applications for weaknesses and vulnerabilities. There are several different kinds of vulnerability scanners available today. Some scanners are limited to assessing certain forms of vulnerabilities, others assess only certain places within the system for problems, and some more advanced scanners that will assess an entire network. The more advanced vulnerability scanners are also equipped to perform what is referred to as network reconnaissance. This allows authorized users to see exactly what computers are connected to the network in live time. This system makes identifying threats and or potential hackers easier than ever before. Vulnerability scanners are a crucial part of most businesses that store sensitive or private data and information.
There are certain state and federal regulations and guidelines put in place in regards to network vulnerability assessment. This is especially true in cases such as government and federal buildings and organizations.
Network vulnerability assessment is an important part of today’s technology-reliant world and data security within business.